Achieve Company Continuity With Secure Cloud Storage Solutions
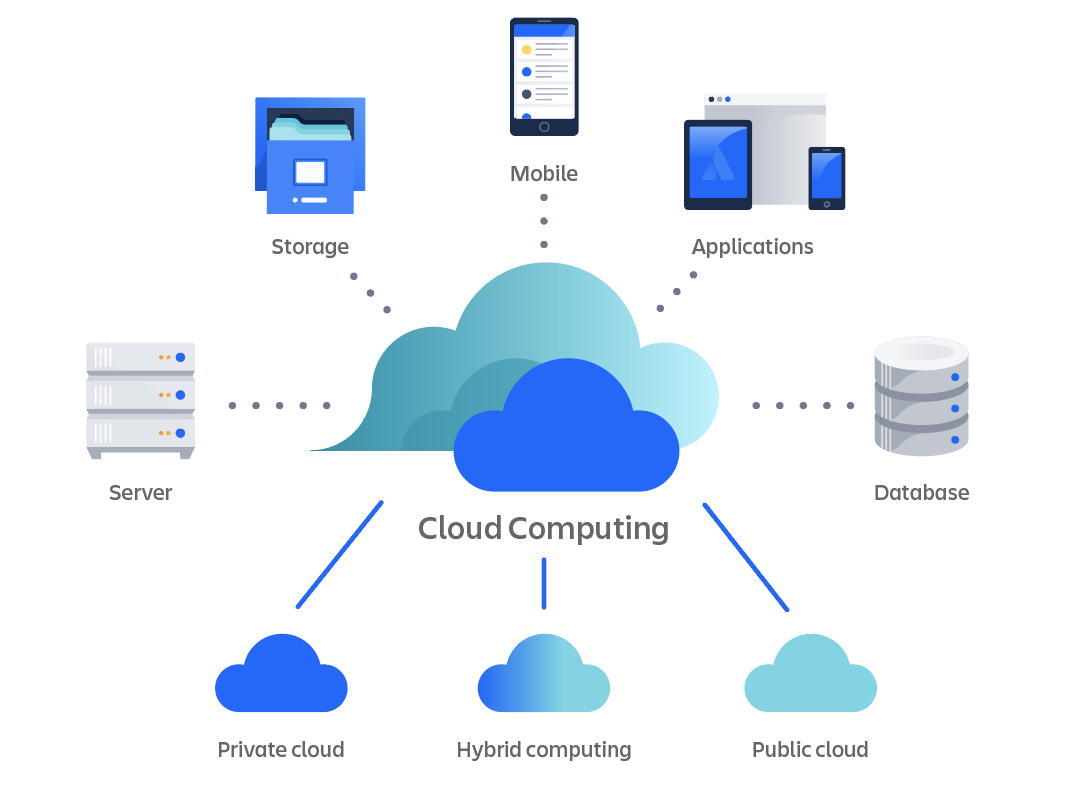
Advantages of Secure Cloud Storage
Undoubtedly, secure cloud storage offers businesses a multitude of benefits in terms of information defense and availability. By keeping data on trusted cloud platforms that employ encryption and innovative protection procedures, services can protect their information from unapproved accessibility or cyber dangers. Generally, the benefits of secure cloud storage translate right into boosted data management, raised functional efficiency, and boosted protection for services of all sizes.
Trick Features for Business Connection
By distributing data across various web servers or information facilities, businesses can mitigate the threat of data loss and make certain continual access to their details. Overall, these crucial attributes work with each other to form a comprehensive service connection method that safeguards essential data and procedures.
Significance of Data Security
In today's interconnected electronic landscape, guarding delicate information is extremely important, making the value of data file encryption a fundamental aspect of preserving information integrity and protection. Information file encryption includes inscribing info as though only licensed events can access and understand it. By transforming data right into a secure layout, file encryption acts as a shield versus unapproved accessibility, minimizing the risk of information violations and cyber risks.

Disaster Recuperation Methods
Efficient disaster recuperation methods are vital for businesses to make sure and reduce possible interruptions see this page continuity despite unexpected occasions. A robust calamity healing strategy includes outlining treatments to recover information, applications, and IT infrastructure in the occasion of a disaster. One crucial aspect of a reliable technique is normal data back-ups. By storing data in safe and secure cloud storage space solutions, businesses can make sure that important info is safeguarded and conveniently available in instance of a disaster. Checking the disaster healing strategy routinely is additionally crucial to determine any kind of weaknesses and make required renovations. Additionally, having an assigned group responsible for carrying out the recuperation strategy can minimize and streamline the process downtime. It is crucial to take into consideration various disaster situations and customize the recuperation approaches to address particular dangers that the service might encounter. By implementing detailed disaster recovery techniques, services can improve their strength and secure their procedures versus unpredicted occasions.
Selecting the Right Company
To ensure smooth service continuity and effective calamity healing, selecting a reliable and ideal provider for protected cloud storage space is vital. When picking a cloud storage space company, numerous essential Click This Link factors need to be thought about. Evaluate the copyright's safety and security measures. Guarantee they employ robust security techniques, have rigorous gain access to controls, and abide with industry laws to protect your information. Additionally, examine the provider's data recuperation capabilities. A reputable provider should use normal backups, redundancy procedures, and reliable recovery processes to decrease downtime in case of a catastrophe.
Moreover, take into consideration the scalability and adaptability of the cloud storage space solution. Your organization demands might progress gradually, so it's important to pick a provider that can accommodate your expanding storage space needs and adjust to altering situations. Finally, analyze the service provider's record and credibility in the industry. Search for reviews, testimonials, and study to evaluate their reliability and efficiency. By thoroughly evaluating these aspects, you can choose view a cloud storage space company that lines up with your company's needs and guarantees constant operations despite possible interruptions.
Verdict
Finally, secure cloud storage space solutions offer vital advantages for attaining company connection, including boosted safety attributes, seamless scalability, efficient collaboration devices, robust information back-up mechanisms, and calamity healing methods. Data encryption plays a vital function in guarding delicate details, while choosing the appropriate service supplier is crucial to ensuring compliance with policies and preserving functional performance. linkdaddy cloud services press release. Safe and secure cloud storage is an important possession in today's digital landscape for making sure continuous organization operations
Information backup mechanisms are critical for protecting against information loss due to system failures, cyber-attacks, or human errors. By distributing data across different servers or data centers, organizations can reduce the risk of data loss and make sure continual accessibility to their details.In today's interconnected digital landscape, securing delicate info is critical, making the relevance of data file encryption an essential facet of preserving data stability and safety and security. By transforming information right into a protected layout, file encryption acts as a shield against unapproved gain access to, minimizing the threat of data breaches and cyber risks.
Compliance demands and data protection regulations commonly mandate the use of security to protect sensitive information, highlighting its vital function in modern information safety approaches.